Include a Bitbucket markdown file
Here is a markdown file from the public repository atlassian/atlassian-jwt-js available at this url: https://bitbucket.org/atlassian/atlassian-jwt-js/src/master/README.md.
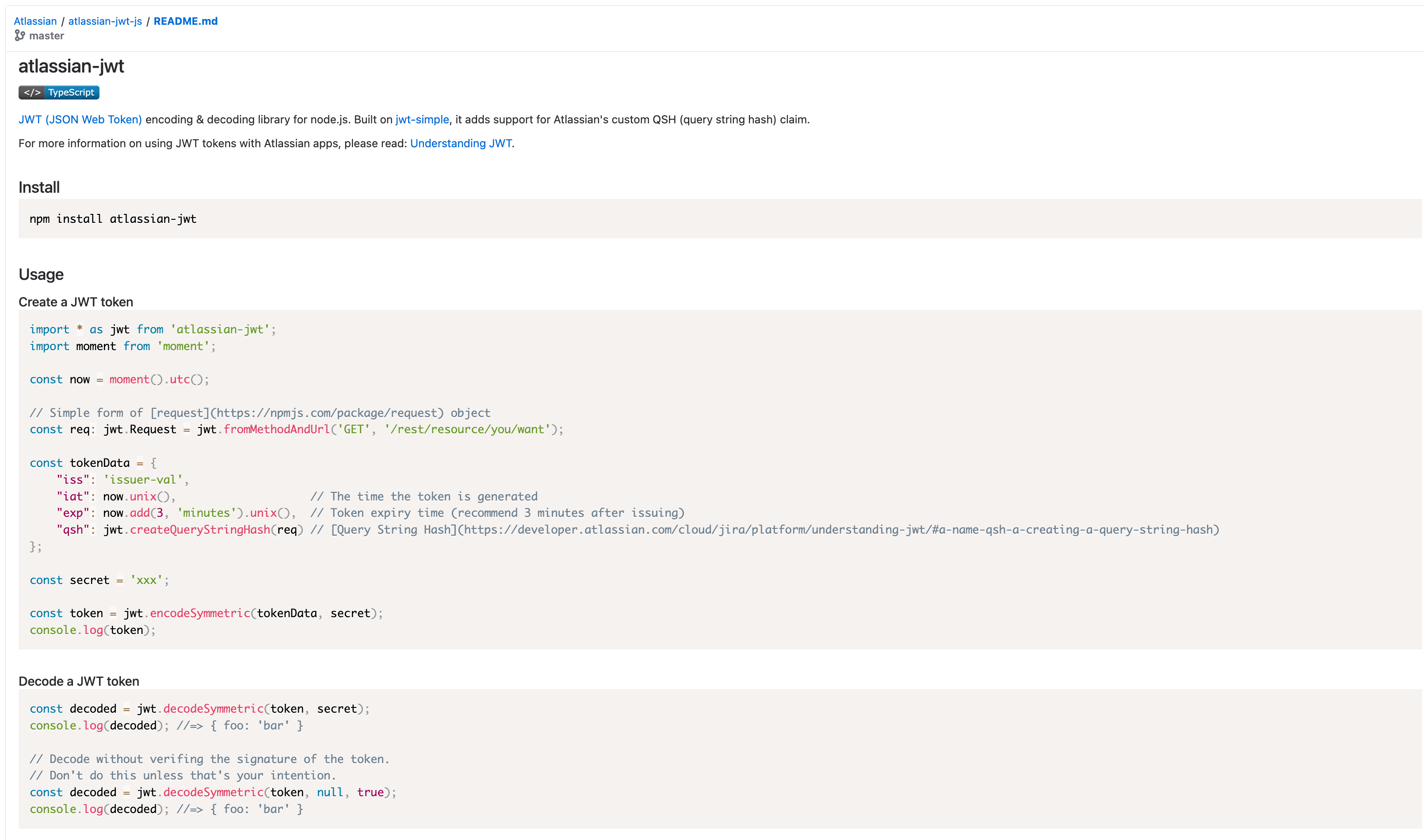
Include a Bitbucket source code file
Here is a typescript file from the public repository atlassian/atlassian-jwt-js available at this url: https://bitbucket.org/atlassian/atlassian-jwt-js/src/master/test/signed_url_interoperability_test.ts.
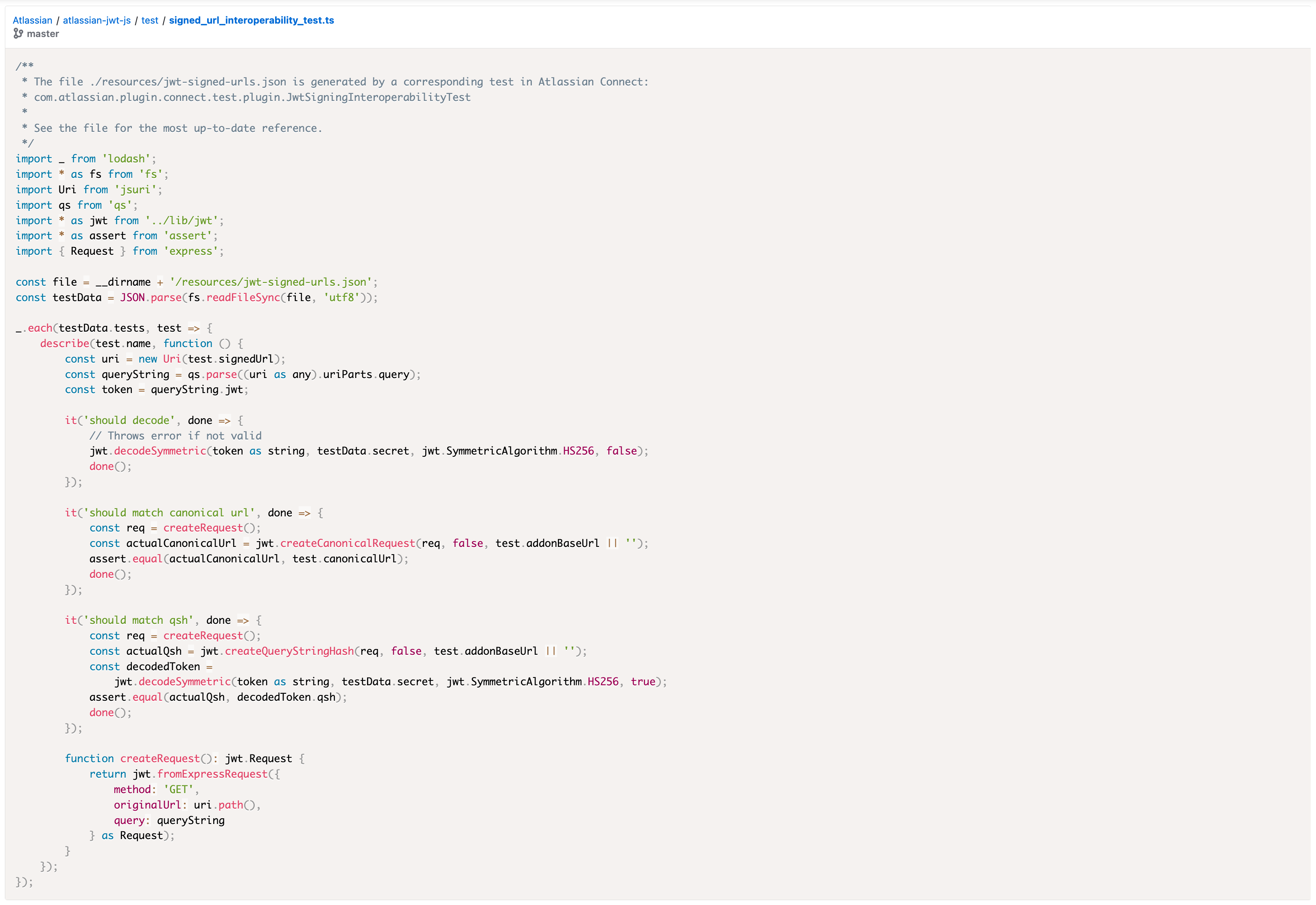
Include Bitbucket pull requests
Here is an example of including the Pull Requests from the public repository atlassian/atlassian-jwt-js with the filters state="MERGED" AND title~"fix":
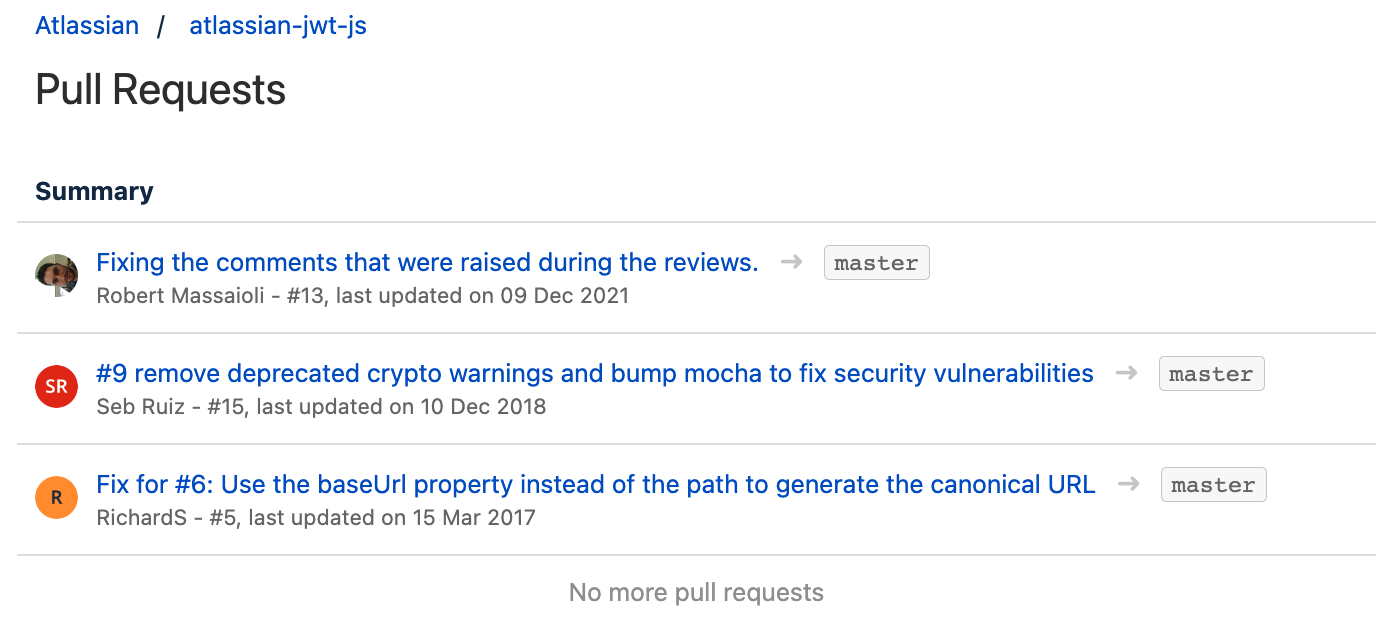
|
Include Bitbucket branches
Here is an example of including the branches from the public repository atlassian/atlassian-jwt-js :
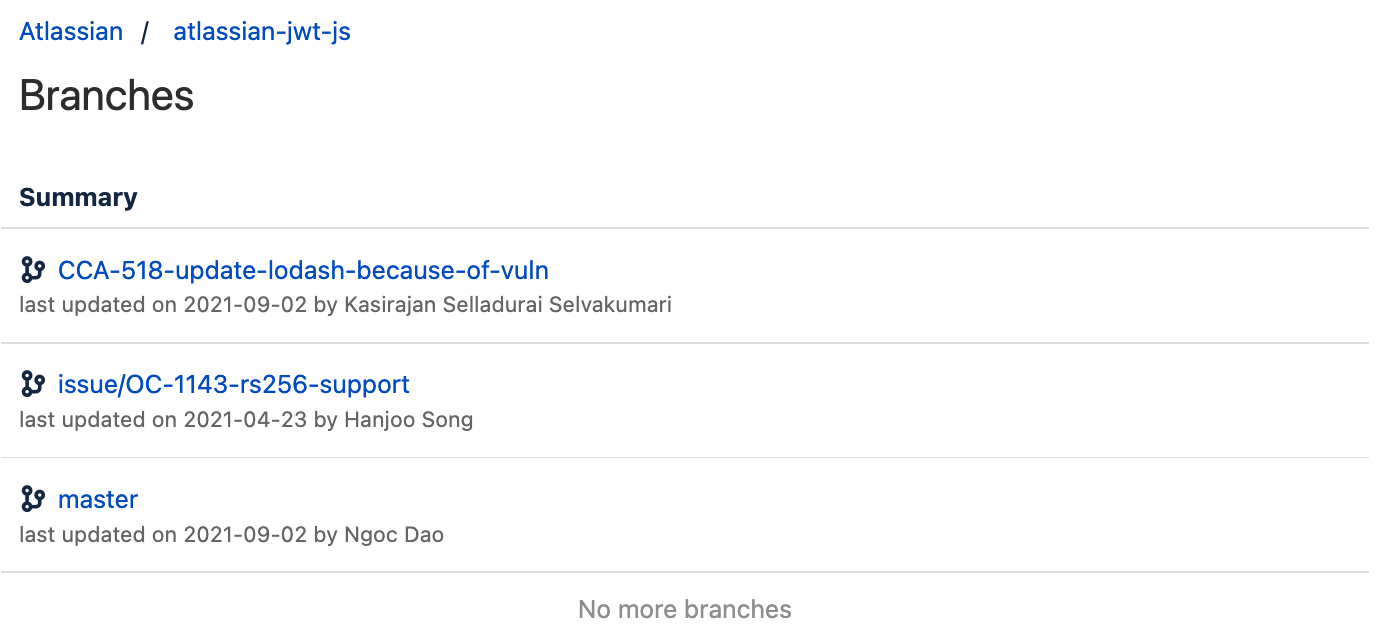
|
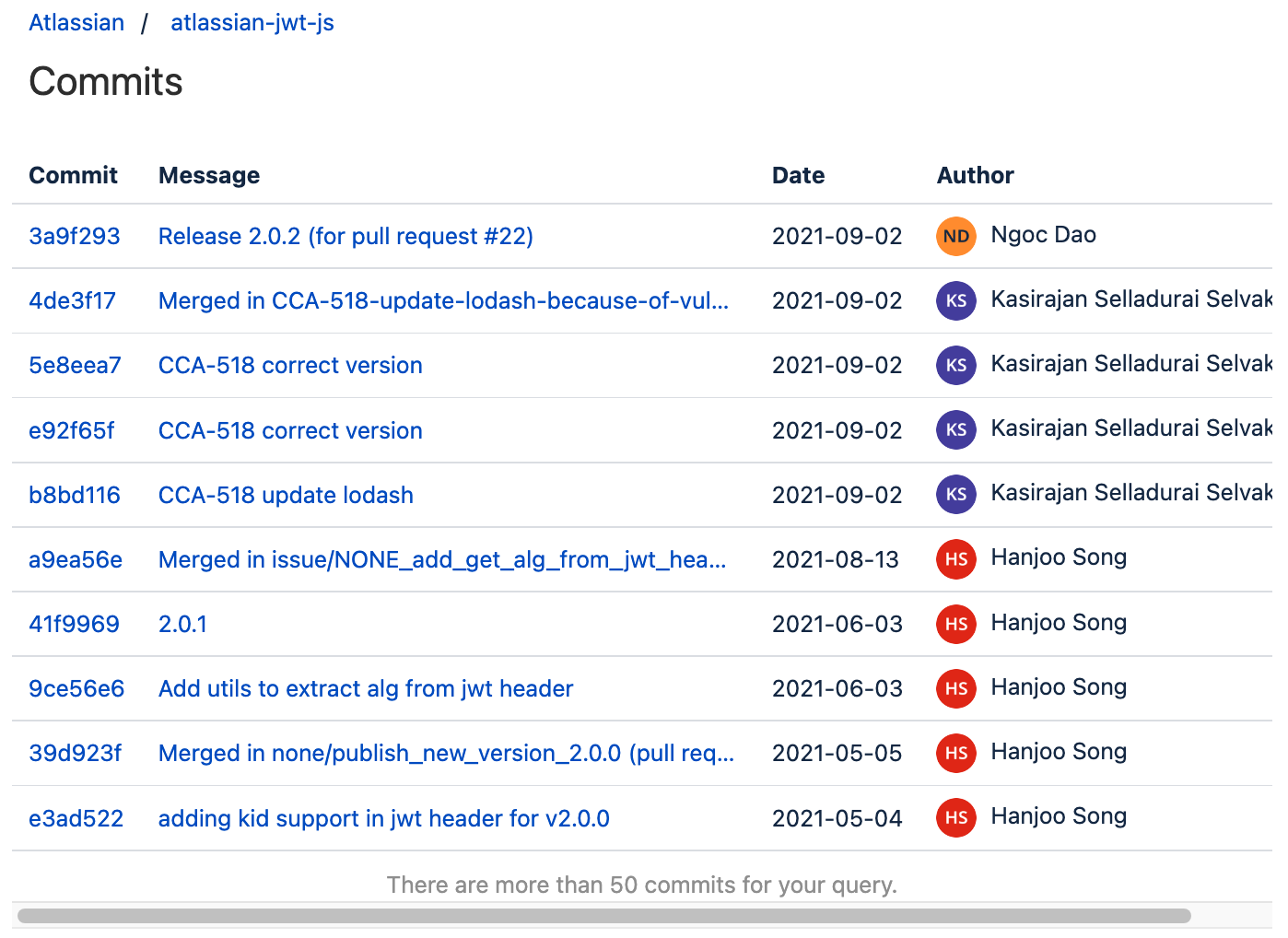
Include Bitbucket commits
Here is an example of including commits from the public repository atlassian/atlassian-jwt-js :
|
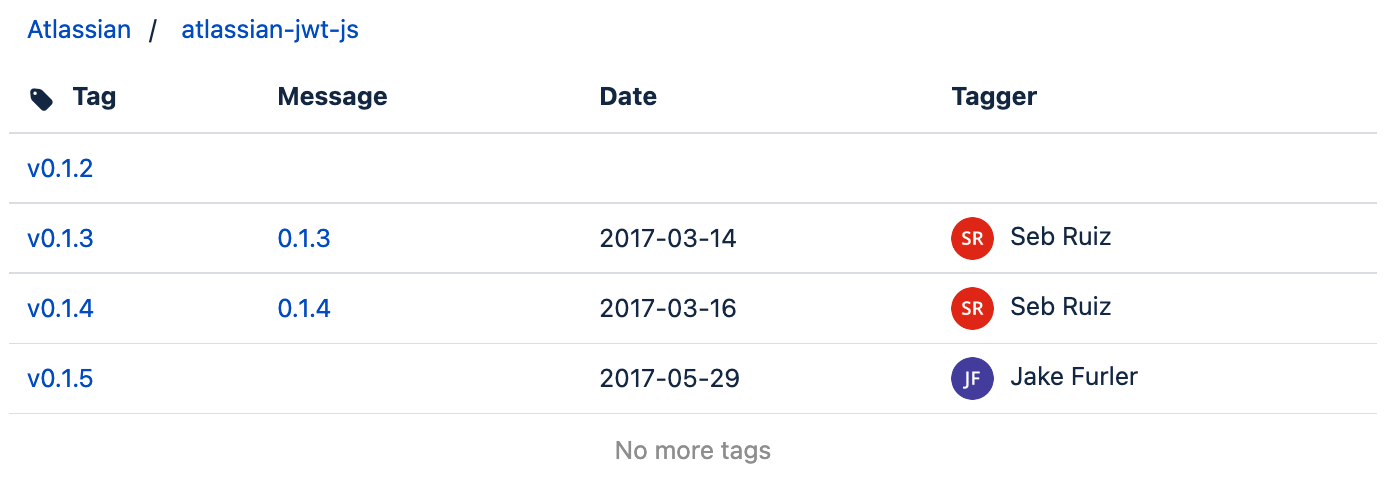
Include Bitbucket tags
Here is an example of including the tags from the public repository atlassian/atlassian-jwt-js :
|
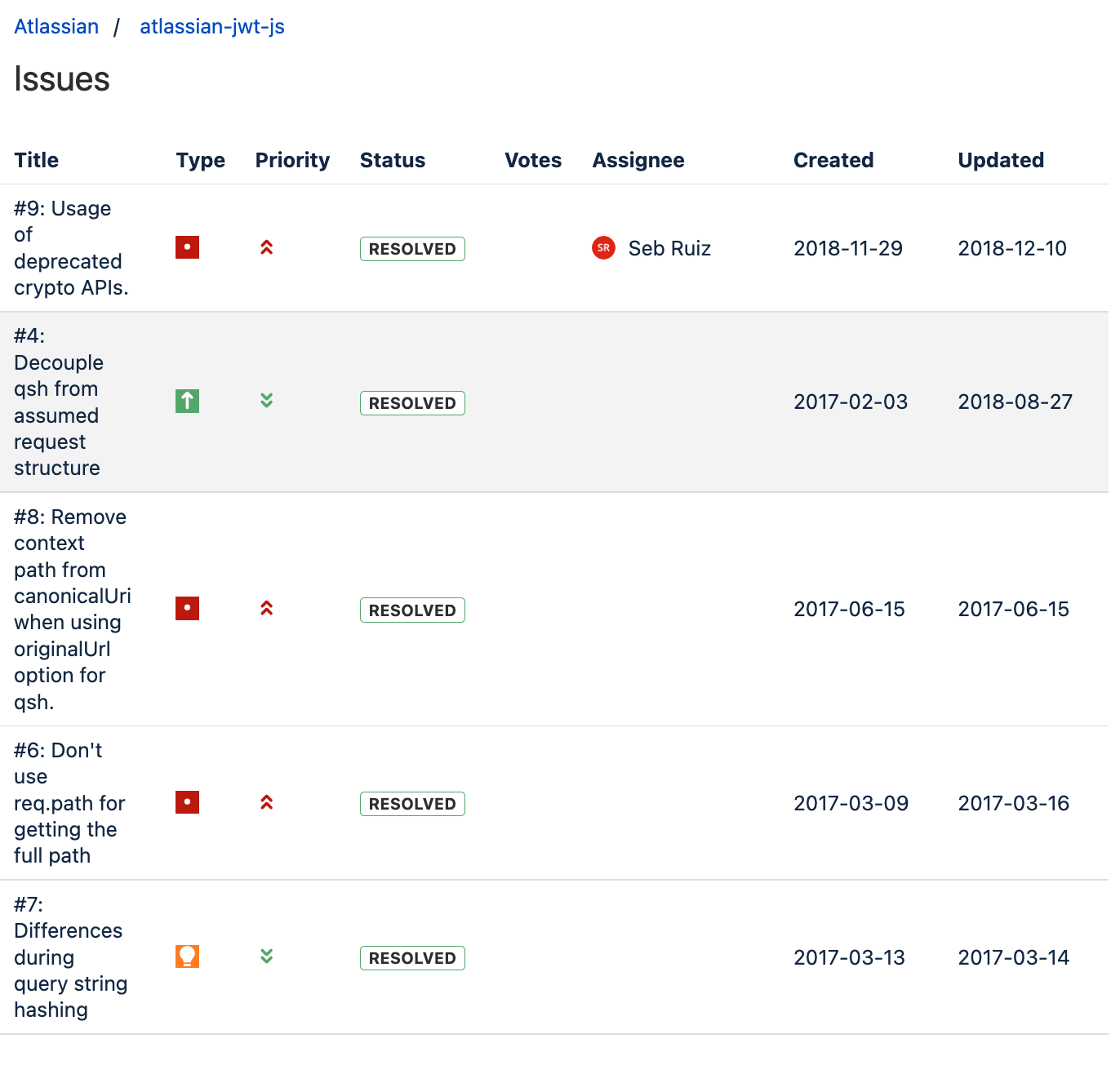
Include Bitbucket issues
Here is an example of including the issues from the public repository atlassian/atlassian-jwt-js with the filters state="resolved":
|
